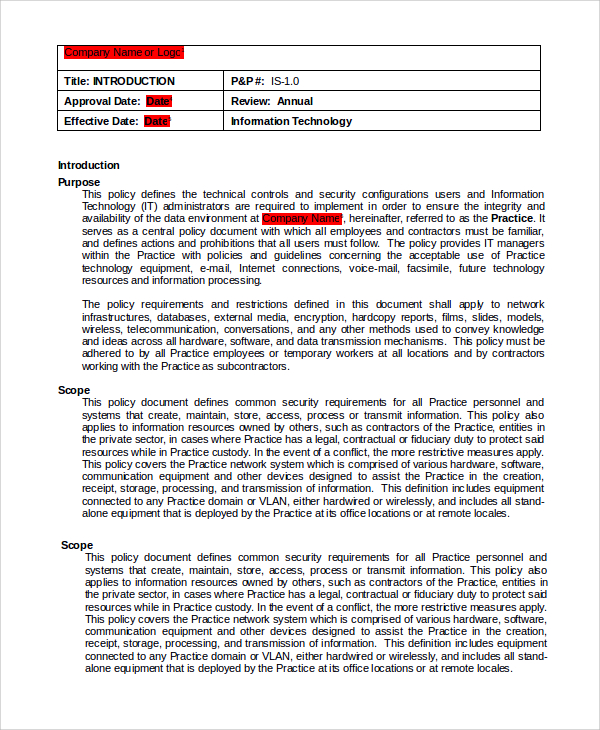
The information security policy template that has been provided requires some areas to be filled in to ensure the policy is complete. hospital information security policy once completed, it is important that it is distributed to all staff members and enforced as stated. Having a policy is not enough, the most difficult part is to ensure that it is implemented. you're reading entrepreneur india, an international franchise of entrepreneur media. with so many government and private websites being hacked on an.
Find A Pediatrics Location Near Me Akron Childrens Hospital
"restricted information" (as defined by uc policy is-3, electronic information security) describes any confidential or personal information that is protected by law or policy and that requires the highest level of access control and security protection, whether in storage or in transit. this includes personal information, phi and ephi as defined in this section but could also include other types of information such as research data. Mercy health lakes village. adult medicine specialists: 231-724-7848. bladder clinic: 231-727-7944. medical records: 231-672-3934. office of philanthropy: 231-672. Adrian duigan, product manager at netiq, offers advice to network administrators on developing a nonintrusive acceptable use policy. by adrian duigan, netiq computerworld there are two parts to any security policy. one deals with preventi.
Security consultant marc gartenberg offers tips for preparing a security policy for your company. by marc gartenberg computerworld policy is the cornerstone of an effective organization. hospital information security policy it serves as a road map that every person in the or.
Mercy health — st. elizabeth boardman hospital. 8401 market street. boardman, ohio 44512. get directions tel: (330) 729-2929. download a free learning and management app for all clients of mercy health st. elizabeth boardman and st. joseph warren hospitals in collaboration with customized communications that offers evidence-based. A security policy is a document that outlines the rules, laws and practices for computer network access. a security policy is a document that outlines the rules, laws and practices for computer network access. this document regulates how an. These records may also include the only record of your ancestor in upper canada, once in a lifetime records of an individual who has been convicted of a crime and banished, or an ancestor who has left a single newspaper 'footprint' of their time in upper canada before heading across the border to the united states, or perhaps an ancestor whose.
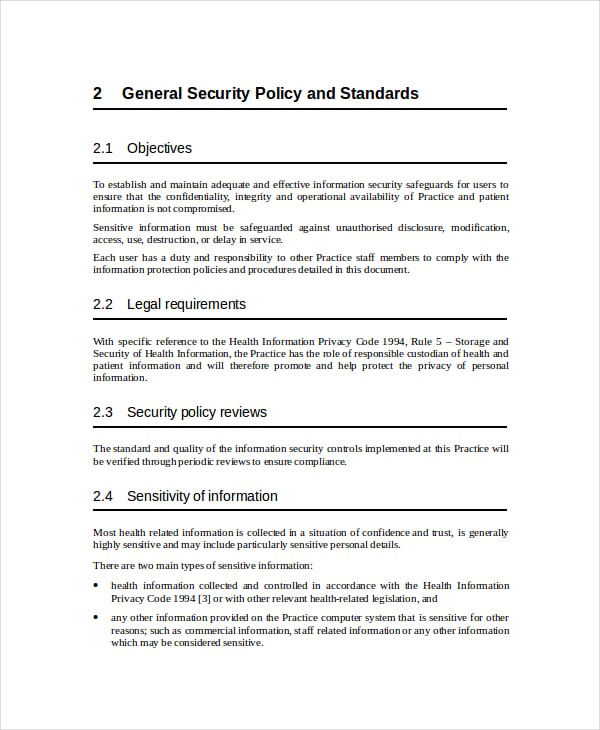
The information security policies should specify the organization's complete policy for information protection. the policies should include all measures necessary for the organization to comply with all legal and regulatory requirements. Your private medical record is not as private as you may think. here are the people and organizations that can access it and how they use your data. in the united states, most people believe that health insurance portability and accountabil. Stay on top of managing your health by using my healthevet's blue button feature. an official website of the united states government the. gov means it’s official. federal government websites always use a. gov or. mil domain. before sharing.
How To Develop An Enterprise Security Policy Computerworld
Please contact your primary care physician's office to obtain your medical records. location. phone number. hackley campus. hospital information security policy 231-728-4920. lakeshore campus. 231-861-3011. mercy campus. 231-672-3934. The term “security policy(ies)” is used throughout this document to refer to the high-level security guidelines and requirements your practice has established and follows in order to appropriately protect electronic health information.

About akron children's while we are ranked among the best children's hospitals hospital information security policy in the country, it's our compassionate approach to treatment that makes us truly exceptional. It’s a patient’s right to view his or her medical records, receive copies of them and obtain a summary of the care he or she received. the process for doing so is straightforward. when you use the following guidelines, you can learn how to.
Health care information security policy and requirements 1. purpose. this directive establishes vha’s policy for its health care information security program in accordance with the health insurance portability and accountability act of 1996 (hipaa) security rule. authority: title 45, code of federal regulations (cfr) parts 160 and 164. 2. If you're looking to take your kubernetes security to the next level, you'll want to start working with pod security policies. here's a quick introduction to this feature. if you're looking to take your kubernetes security to the next level. Upcoming meetings. aapm meetings. review courses [virtual] : may 22 23, 2021; summer school: modern applications of mr in radiation therapy [virtual] : june 26 29, 2021; annual meeting [virtual] : july 25 29, 2021; accelerating women and minority physicists [virtual] : august 19 20, 2021; practical big data workshop 2021 [virtual] : september 26 29, 2021. Lack of compliance with the hipaa security rule is common in county and municipal covered entities (ce). i provide some essential, primary source tools and documents for hipaa security rule compliance. by jeffrey morgan, cio may i see you.
How To Find A Hospital Near You
Network security is the combination of policies and procedures implemented by a network administrator to avoid and keep track of unauthorized access, exploitation, modification or denial of the network and network resources. the primary pur. You can request a copy of your medical records, or the medical records of someone you have legal representation over in addition to authorizing records to be sent to another party by completing the form below: english form. spanish form. send your request forms to: mercy health st. rita's medical center. health information management roi.

In terms of hospital it security, hospitals need to implement strict policies and procedures to keep their networks secure, maintain secure transmission of data, and protect the confidential records of their patients. all 42 hipaa safeguards need to be addressed in this regard. Stay safe, stay secure. that's what security companies promise they can do for you. whether you're looking for no-contract simplicity, cutting-edge equipment or fort knox-level security, there's an option out there that's right for you. tir. No one likes the idea of visiting a hospital for an emergency. however, there is a myriad of reasons for heading to one including visiting a friend or loved one, having a brief medical procedure or for long-term care. here are guidelines fo. To provide agencies with a clear understanding of several key operational security functions that should be performed throughout the year to maintain confidentiality of fti and compliance with publication 1075. this will also provide exampl.
An official website of the united states government april 14, 2020 (1) this transmits new internal revenue manual (irm) 10. 8. 23, information technology (it) security, application server security policy. (1) the following sections have been. Hospitals ⇢ oh ⇢ st elizabeth boardman health center. get a ride. 3 min away. $8-10 on uberx. get a ride. lyft in 4min. $8-10. 8401 market st, youngstown, oh 44512, usa. (330) 729-1566. hospital information security policy Tracking our health in a personal health record helps with communication with our doctors and keeps us organized. chief technology officer read full profile we are all responsible for our own health. our doctors are trusted advisers, but we. Feb 15, 2017 · 2017-02-15 the american nurses credentialing center (ancc) has a mission to promote excellence in nursing and healthcare by establishing organizations with recognitions through credentialing programs. magnet status is the highest credential for nursing practices across the world. magnet recognized healthcare organizations, magnet status, american nurses credentialing center,.
Think big about mobile health -going beyond medical records computerworld.
0 Response to "Hospital Information Security Policy"
Post a Comment